Calem Blogs
How to Customize Access Control/ACL Profiles in Calem
Access control in Calem allows administrators to assign users to access control list profiles (ACL Profiles). An ACL profile includes permissions of application functions and sites's data for multi-site data access. This blog discusses the setup of ACL profiles.
Here is a use case for ACL Profiles for multi-site access:
- An organization has 3 sites (A, B and C) each has own resources, assets and inventory. Supervisors will have access rights to all three sites while technical staff only have access to their own site with limited functions.
- A supervisor ACL Profile "All-Supervisors" is created for the supervisors.
- A "Supervisors" group is created with access to all functions.
- The group is used to create the ACL Profile "All-Supervisors" with access to all sites' data.
- An ACL Profile (SiteA-Techs) is created for the technical staff of SiteA. The technical staff need edit rights of the asset and work order modules, and read-only rights of the inventory module.
- A "Techs" group is created with the access rights of modules (edit of asset and work order modules, read-only of inventory).
- The ACL Profile "SiteA-Techs" is created from group "Techs" with access to SiteA's data.
- An ACL Profile (SiteB-Techs) is created for the technical group of SiteB.
- SiteB-Techs reuses the "Techs" group and allows access to SiteB's data.
- "SiteC-Techs" is created for the SiteC's technical users.
- "Techs" is re-used again, and SiteC's data is granted in the ACL Profile "SiteC-Techs".
- So, identifying user groups is the first step in multi-site access control design in Calem.
- A user group represents users of the same job roles. Sample user groups include technical staff, supervisors, and warehouse staff.
- A user group can be defined once and re-used in ACL Profiles with different access to sites' data, and other attributes.
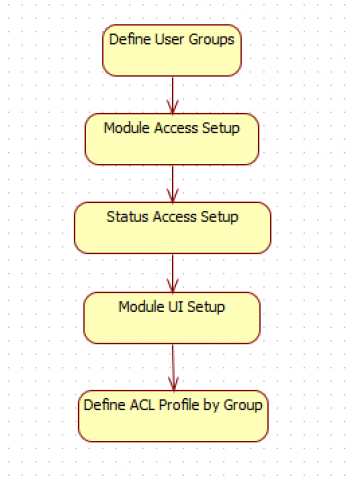
Step 1. Define User Groups
Groups are used in Calem to represent users of the same job roles. For instance, maintenance technicians can be represented by a group "Maint-Techs".
- See Step 1 of this blog for group creation.
Step 2. Module Access Setup
This step defines the modules granted to a group, and module functions granted to a group.
- See this blog for the Module Access Setup.
- See this blog to set up a module as read-only for a group.
Step 3. Status Access Setup
Work order status access can be configured for the group. For instance, technicians cannot approve or accept work orders.
- See this blog for the Status Access Setup.
Step 4. Module UI Setup
Module UI customization includes the following items:
- List form and menu
- Hide edit menu including "New", "Edit", "Delete" and functional menu items
- Customize fields and order in the list view.
- Read form and menu
- Hide edit, and functional menu items such as "Re-Open WO".
- Customize read form to add/remove fields, or move fields around in the form.
- Edit form
- Add or remove fields editable for a group.
- Add or remove fields that are editable for a group.
- Reports
- Layout customization to add/remove fields
- Search forms
- Add/remove fields in search forms
- Text labels
- Customize text labels
- Multi-Tab Forms
- Add/remove tabs or list forms in a MdTab form
- Move list forms between tabs
- Order list forms in a tab
The following blogs cover some of the customization. There are more information in Calem Admin Guide.
- Calem Enterprise UI Customization
- List View Customization
- Read and Edit View Customization
- Tab customization in Work Order Print Customization
- Text customization in Home Form Customization
- Object Categorization-Based UI Customization
- Mobile Screen Customization
5. ACL Profiles
- See this blog for ACL Profile Setup
- More than one profile can be assigned to a user
- Users with more than one profile assigned will have a choice to select a profile to sign into Calem.
Related Posts
By accepting you will be accessing a service provided by a third-party external to https://eam.calemeam.com/