Calem Blogs
Steps to Implement Risk Assessment in Calem
Risk Assessment Module is added in Calem in the coming release of R2024e (September 2024). This blog presents the steps to implement Risk Assessment in Calem.
The Risk Assessment module may be used to manage life cycles of risks including potential risk identification and documentation, analysis and evaluation, and the development of mitigation steps. It is part of the management of health, safety and environment (HSE).
1. What is an Risk Assessment?
Risk assessment is a systematic process used to identify, analyze, and evaluate potential risks that could negatively impact an organization or project. It is critical for proactively managing potential threats to an organization or project.
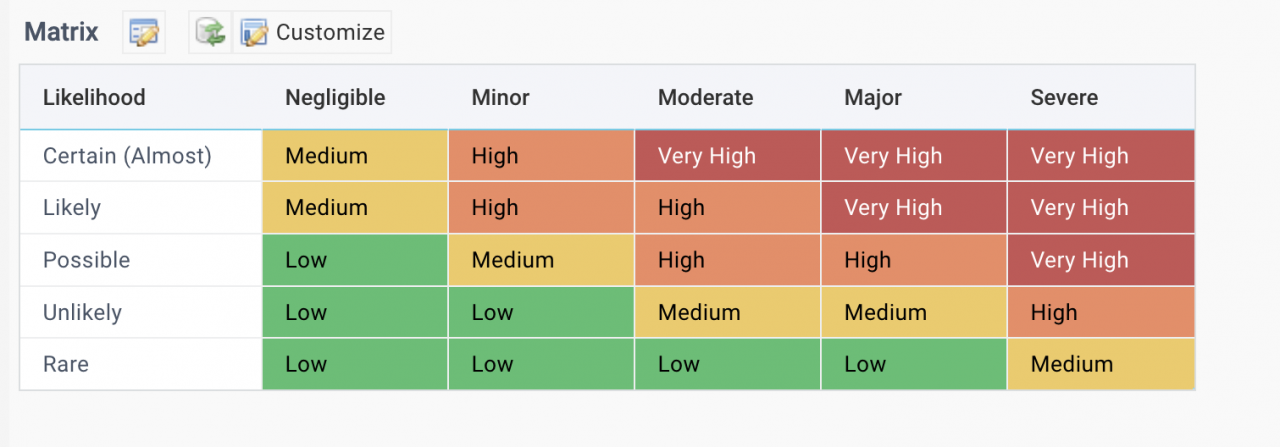
2. Risk Matrix
A risk matrix can be configured by Risk Planners. It is a matrix for an organization to determine risk levels and priorities.
- A sample risk matrix is show below.
- A Calem admin can create the sample matrix by uploading a) a risk matrix entry (cm_risk_rmx.RiskMatrix.xls) ; and b) the risk matrix lines (cm_risk_rmx_det.RiskMatrixDet.xls).
- Risk Planners can create, and edit a risk matrix directly and save changes in the web UI.
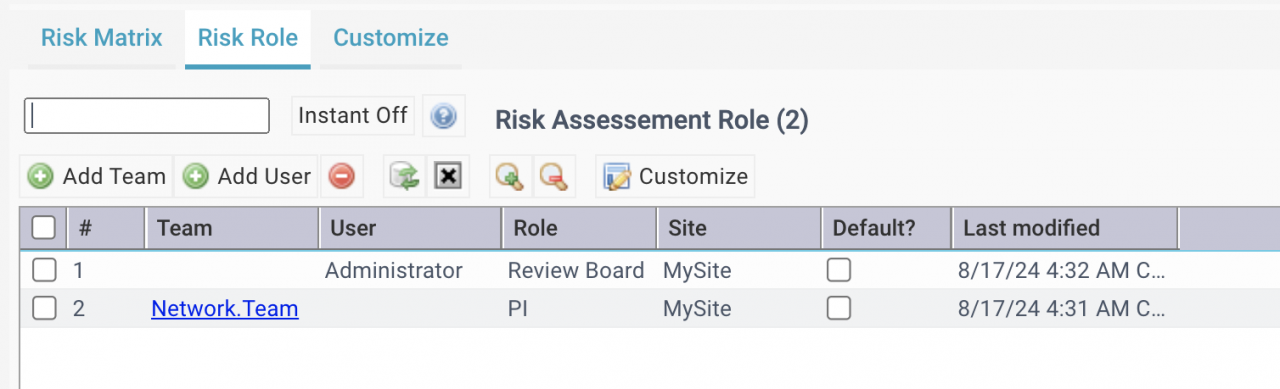
3. Risk Assessment Roles
Roles for risk assessment including risk planners, monitors, principal investigators (PI), review board and others.
- Risk Roles: Organization | ACL Profiles | Risk Assessment
- They include a) Principal Investigator; b) Review Board; and c) Others.
- They are assigned to sites.
- A principal investigator may be designated as default by site.
- Investigators can be assigned to risk actions.
- Users or teams can be assigned to roles by site (screenshot below).
- Risk Planners and Monitors:
- Menu: Organization | ACL Profiles | Monitor User
- Create teams or users with roles of a) Risk Planner; and b) Risk Monitor
- Risk planners can assign principal investigators to risks by site.
- Risk monitors can receive workflow notifications when risks are changed.
4. Assign Roles to Risks
There are two types of resources to assign to a risk:
- The investigators to work on risk assessment action items including risk analysis and mitigation. They are users assigned to a site.
- The reviewers to evaluate risk assessment reports.
- The resources are assigned to a risk by its PIs.
- These users along with the requester and Risk Planners can modify a risk.
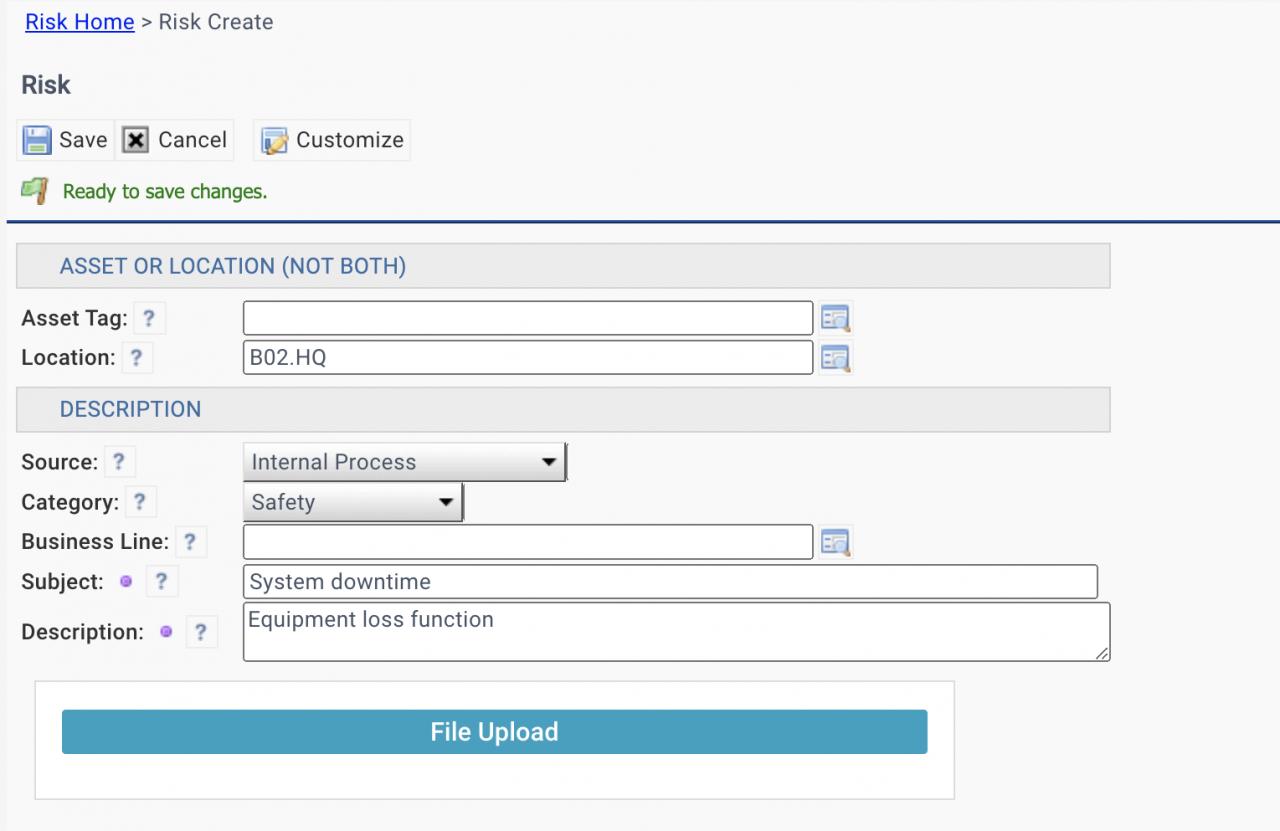
5. Create a Risk
A risk is created by a user with access to the risk module.
- An Asset or Location is required to create a risk.
- Files may be attached when creating a risk.
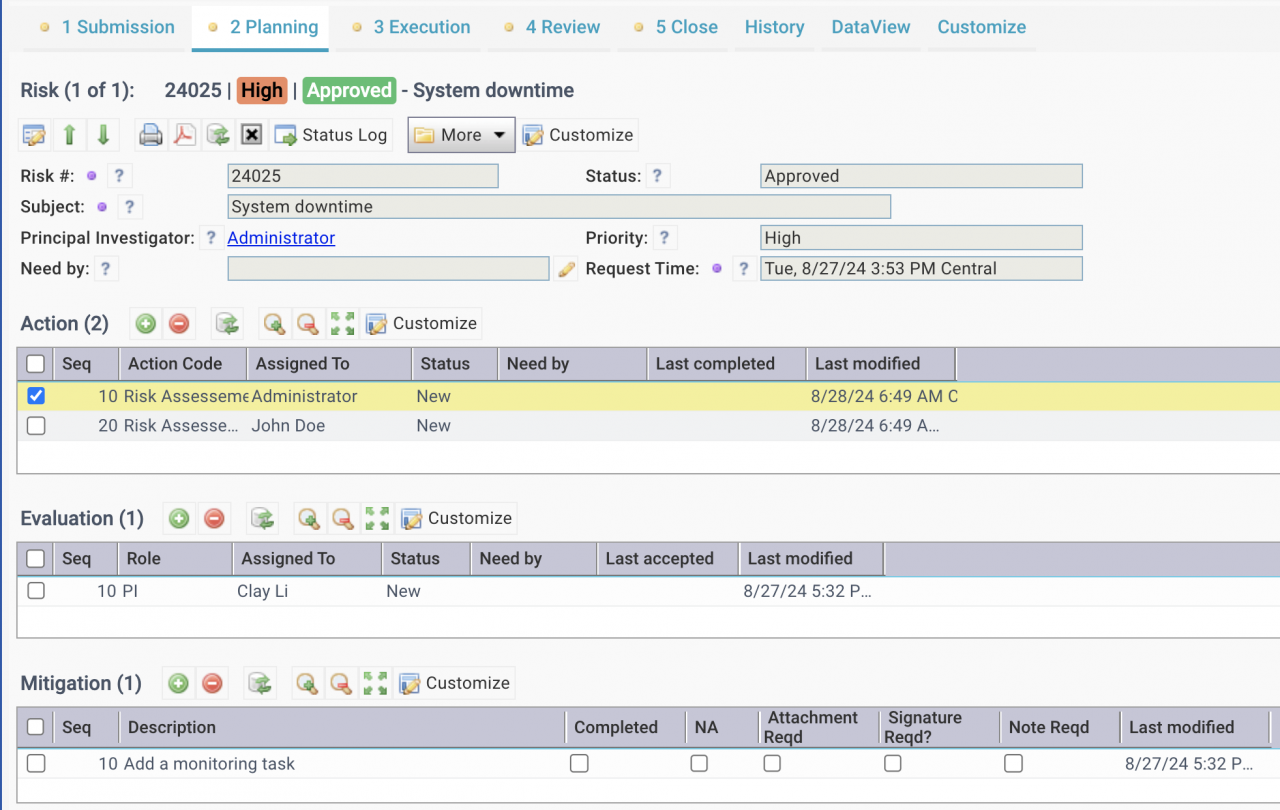
- After a risk is created, a PI (Principal Investigator) needs to be assigned by a risk planner.
- The PI builds a team by assigning users for risk Action and Evaluation (screenshot above).
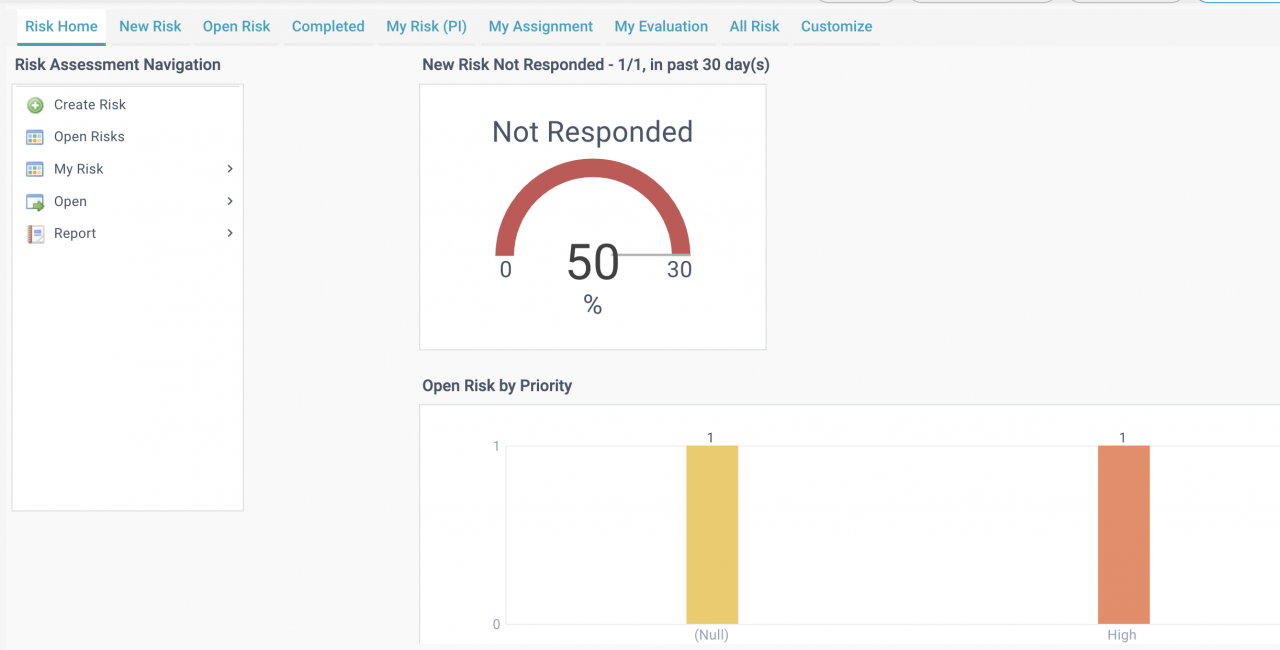
- A home screen is available for Risk Assessment including risk stats, menu, and data lists for quick actions.
- New Risk: new Risks not processed
- Open Risk: Risks in process, not completed or accepted.
- Completed: Completed Risks ready for evaluation.
- My Risk (PI): Risks with login user being a principal investigator.
- My Assignment: Open risks with login user as an investigator.
- My Evaluation: Open risks with login user as reviewer.
- All Risk: All risks accessible to the login user.
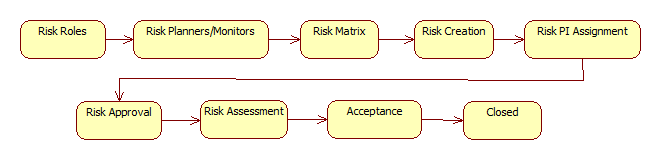
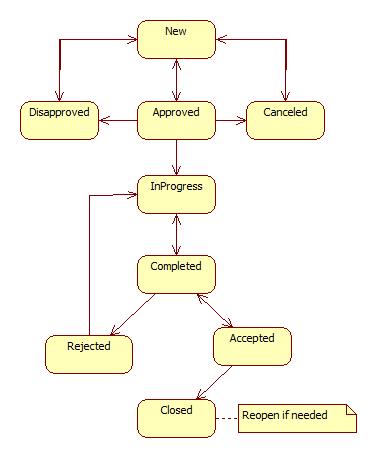
6. Risk Lifecycles
Only Principal Investigators (PI for a risk) can modify risk statuses.
- Additional PIs can be added to a risk as evaluation member with the PI role.
- A risk action can be completed by the user assigned to it or a PI.
- A risk mitigation step can be completed by users assigned to actions.
- A risk evaluation can be completed by the user assigned to it or a PI.
- A risk cannot be completed if there are unfinished actions.
- A risk cannot be accepted if there are unfinished evaluation tasks.
Additional Resources
- Steps to Implement CAPA in Calem
- Steps to Implement Incident Module in Calem
- Why Implementing Change Management (MOC) in Calem
- Work Permits in Calem
- Work Order Module Training
- Service Request Module Training
- User Guide and Admin Guide (customer account required)
- Calem Enterprise Training Site
- Calem Enterprise Blogs
- Calem Enterprise demo
By accepting you will be accessing a service provided by a third-party external to https://eam.calemeam.com/